In today’s hyper-connected world, smartphones have transcended their function as mere communication devices; they have become integral to both personal and professional lives. With sensitive information ranging from financial details to personal appointments stored in these handheld devices, the demand for secure smartphone environments has never been more pressing. Yet, a recent study from researchers at TU Graz has revealed alarming vulnerabilities within the Android kernels utilized by prominent smartphone manufacturers. This article will dissect the key findings from the study, examine their implications, and discuss the broader ramifications for smartphone security.
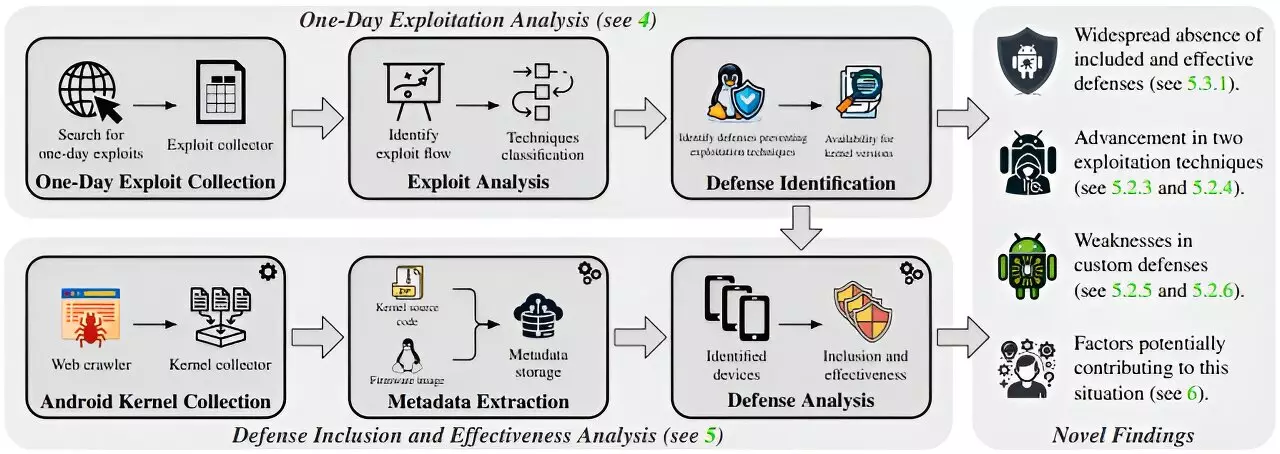
The research team at TU Graz, comprising Lukas Maar, Florian Draschbacher, Lukas Lamster, and Stefan Mangard, analyzed the Android kernels of the ten largest smartphone manufacturers, unveiling numerous weaknesses that expose users to attacks known as one-day exploits. Despite existing security measures, the findings indicate that only a fraction of the devices investigated—ranging from 29% to 55%—successfully thwarted these attacks. This reveals a disconcerting trend of manufacturers prioritizing speed and functionality over comprehensive security, leaving users vulnerable.
With the analysis taking place between August 2018 to 2023, the testing encompassed a significant portion of the smartphone market. The results, presented at the Usenix Security Symposium, demonstrated a particularly stark contrast between the Generic Kernel Image (GKI) 6.1 offered by Google and the various manufacturer-specific kernels. The GKI was capable of preventing approximately 85% of security threats, while the proprietary kernels lagged, showing performances that were up to 4.6 times less effective in counteracting attacks.
The research highlighted that many vulnerabilities were not new; they were known issues that had existing countermeasures which, tragically, were either not activated or were incorrectly configured on various manufacturers’ kernels. For instance, kernels as dated as version 3.1 from 2014—when fully secured—outperformed over a third of the more recent kernels in defending against known threats. This raises critical questions about manufacturers’ commitment to ongoing security improvements and their responsibility to harness the full potential of available protective technologies.
Moreover, the findings suggested a concerning trend where low-end models are disproportionately affected by security flaws. Low-cost devices exhibited a 24% higher risk due to potentially deactivated security measures aimed at conserving performance. This trade-off between resource allocation and security could lead users of budget smartphones to operate under the illusion of safety while exposing sensitive information to increased risk.
The implications of this research reverberate across the tech industry, particularly regarding manufacturers’ accountability in safeguarding user data. Companies such as Google, Fairphone, Motorola, Huawei, and Samsung have been informed of these vulnerabilities, prompting some to release patches. However, while these updates may represent a step in the right direction, they also point to a reactive rather than proactive security strategy.
The study’s authors advocate for systematic changes, urging Google to revise the Android Compatibility Definition Document (CDD), which dictates the security standards expected from devices. Such changes could establish clearer guidelines for manufacturers, reinforcing security as a foundational component rather than an afterthought.
The researchers at TU Graz hope that their findings will not only elevate awareness around these critical issues but also catalyze manufacturers to adopt more robust security protocols. The continual evolution of attack methods necessitates an unwavering commitment to security from both developers and manufacturers alike. Integrating necessary security measures into the overall kernel architecture will be vital for fostering a safer Android ecosystem.
It is evident that amidst the rapid technological advances, vigilance and proactive measures must prevail in the approach to smartphone security. As users, understanding these challenges and advocating for better security measures is crucial. Ultimately, the responsibility for cybersecurity must be shared across all stakeholders—from developers to manufacturers to consumers—to create a more secure digital environment for everyone.